In today’s digital age, cybersecurity has transcended from being an IT concern to a core part of business strategy. Organizations face a myriad of threats that can leave sensitive information vulnerable to breaches, making it imperative to regularly reassess and update cybersecurity policies. This article explores the significance of updating your cybersecurity policies, provides actionable steps for implementation, and addresses common questions related to this crucial process.
The Importance of Regularly Updating Your Cybersecurity Policies
Understanding Threat Landscape
Cyber threats are constantly evolving. From sophisticated phishing attacks to ransomware and insider threats, the strategies used by cybercriminals are dynamic. Regularly updating your cybersecurity policies helps organizations stay ahead of these threats and respond to new challenges effectively $4.45 million.. This proactive approach not only protects sensitive information but also preserves the organization’s reputation and trust among clients.
Compliance Requirements
Many industries are bound by regulations that require stringent cybersecurity measures. Failing to comply with these regulations can lead to hefty fines and legal repercussions. Regular reviews and updates of your cybersecurity policies ensure compliance with laws such as GDPR, HIPAA, and PCI-DSS, among others.
Incident Response Preparedness
In the event of a cyber incident, having an up-to-date cybersecurity policy ensures a streamlined response plan. It delineates roles and responsibilities, identifies critical systems, and establishes communication protocols 94% of malware . Regular updates to the incident response section of the policy can enhance an organization’s agility in crisis situations.
Key Elements to Consider When Updating Your Cybersecurity Policies

Risk Assessment
Conducting a risk assessment is the first step in updating your cybersecurity policies. This involves identifying vulnerabilities and threats specific to your organization. Tools such as vulnerability scanners and threat intelligence platforms can aid in this process. Understanding the risks allows your organization to tailor its policy to address identified gaps effectively.
Employee Training and Awareness
People are often the weakest link in cybersecurity. Regularly updating your cybersecurity policies should include employee training programs to ensure that staff is aware of the latest threats and best practices cybersecurity policy templates. A well-informed workforce can significantly reduce the risk of human error, which often leads to security breaches.
Technology and Tools
With the rapid advancement of technology, new tools and applications frequently emerge that enhance security. Regular reviews can help identify if existing tools are still effective or if new solutions are necessary. Consider implementing measures like Multi-Factor Authentication (MFA), endpoint protection, and Intrusion Detection Systems (IDS) as part of your policy update process.
Data Protection Measures
Ensuring data integrity and confidentiality is paramount. Policies should be updated to reflect current data protection measures, including encryption standards, data retention policies, and disaster recovery plans. Additionally, regular audits should verify adherence to these measures, ensuring data is handled securely.
A Strategic Approach to Updating Your Cybersecurity Policies

Schedule Regular Reviews
Establish a regular schedule for reviewing and updating your cybersecurity policies. This could be quarterly, bi-annually, or annually, depending on the nature and size of your organization. Frequent reviews ensure that changes in the threat landscape, technological advances, or operational changes are promptly addressed.
Involve Key Stakeholders
Engage various departments in the policy review process. Including IT, legal, human resources, and management can provide a comprehensive view of potential vulnerabilities and perspectives on the company’s needs. This collaborative approach fosters buy-in and makes the policies more effective.
Document Changes and Rationale
Whenever updates are made, it’s essential to document the changes and the rationale behind them. This not only aids in compliance audits but also creates a historical record that can be useful for future updates. Transparency in the update process can help maintain a culture of security within the organization.
Common Challenges and Solutions
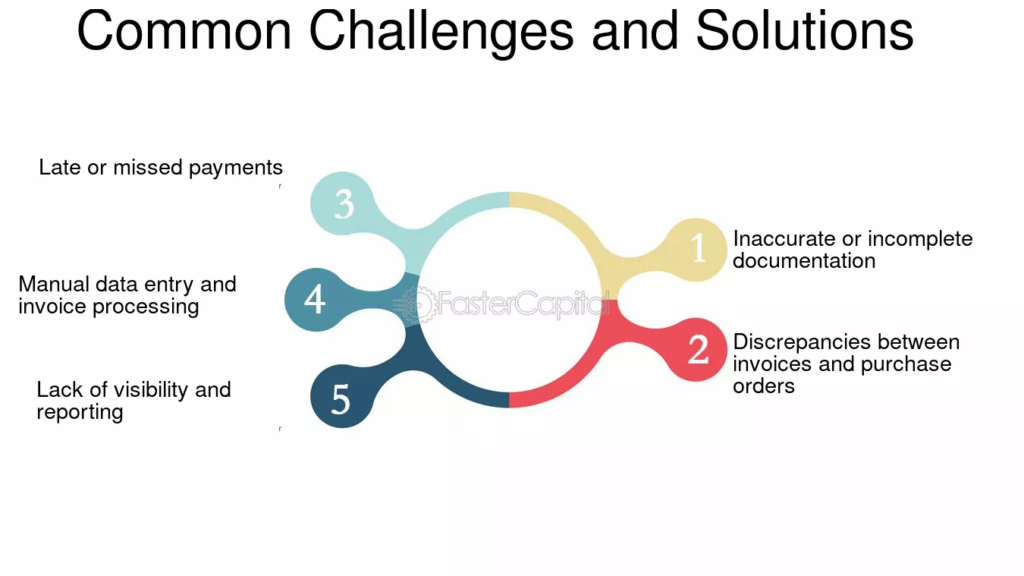
Resistance to Change
One of the major challenges encountered when updating cybersecurity policies can be employee resistance to new protocols. To combat this, engage staff early in the process and clearly communicate the benefits of the changes. Providing adequate training and resources can also mitigate resistance.
Keeping Up with Technological Advances
The rapid evolution of technology means that businesses must adapt quickly. Organizations can join industry consortiums or subscribe to cybersecurity news outlets to stay updated on the latest tools and best practices.
Measuring Effectiveness
After updating your policies, it is crucial to assess their effectiveness through simulations and audits. Regular testing can uncover potential weaknesses in the policy, allowing for continuous improvement.
Conclusion
In a world where cyber threats are ever-evolving, the necessity of regularly updating your cybersecurity policies cannot be overstated. By regularly assessing risks, engaging employees, and staying informed on technological advancements, organizations can significantly improve their cybersecurity posture. Developing a comprehensive approach to policy updates ensures that both sensitive information and the organization itself remain safeguarded against potential threats.
(FAQs) About Updating Your Cybersecurity Policies
1. How often should organizations update their cybersecurity policies?
Most organizations should aim to review and update their cybersecurity policies at least annually, though quarterly reviews are recommended for those in high-risk sectors.
2. What are the penalties for not complying with cybersecurity regulations?
Penalties can vary widely depending on the regulation and severity of non-compliance. Fines can range from thousands to millions of dollars, and companies may also face legal action and reputational damage.
3. How can employee training be effectively implemented?
Tailor training programs to address specific threats relevant to the organization. Utilize various formats such as workshops, online courses, and quizzes to engage employees and reinforce learning.
4. What should be included in an incident response plan?
An effective incident response plan should include a framework for identifying incidents, roles and responsibilities, communication protocols, and recovery strategies.
5. How do we measure the effectiveness of updated cybersecurity policies?
Effectiveness can be gauged through various means, including audits, internal threat simulations, employee feedback, and incident response metrics. Regularly testing and adjusting policies based on these factors enhances overall security.
Read Next: How PKI as a Service Benefits Your Organization: 5 Key Insights
For More Visit: Bratish Magazine